BitHydra: Bit-flip Inference Cost Attacks
Attackers can flip just 3-30 critical bits in LLM memory to force 80-100% of user prompts to generate maximum-length outputs. This revolutionary approach bypasses traditional inference cost attack limitations by targeting the model's weights directly rather than crafting expensive inputs, creating universal impact while the attacker pays nothing.
- Scope: Universal impact affecting all users, not just attacker's queries
- Target Models: LLaMA3-8B, Vicuna-7B, Qwen2.5-14B, Mistral-7B, and other transformer-based LLMs
- Attack Effectiveness: 100% success rate on multiple models with as few as 3 bit flips
Attack Flow
Rowhammer Bit-Flip Process
The Fundamental Breakthrough
Traditional inference cost attacks suffer from a critical limitation: they're inherently self-targeting. The attacker crafts malicious prompts, sends them to the LLM service, and pays for the resulting expensive long outputs. Each attack only affects that specific query, requiring constant expensive inputs to impact other users.
BitHydra's Innovation: Instead of attacking through inputs, directly manipulate the model's memory using hardware-level bit-flip attacks. Flip a few critical bits in the \( \langle\text{EOS}\rangle \) token embedding, and every subsequent user prompt generates maximum-length outputs.
The \( \langle\text{EOS}\rangle \) Token Suppression Strategy
The \( \langle\text{EOS}\rangle \) (End-of-Sequence) token acts as a termination signal in autoregressive generation. BitHydra systematically suppresses this signal by reducing the \( \langle\text{EOS}\rangle \) token's probability through targeted weight modifications.
Normal Generation Process:
User: "What are primary colors?"
LLM computes: P(<EOS>) = 0.85 after "Red, blue, and yellow."
Result: Generation stops at 13 tokens
After BitHydra Attack:
User: "What are primary colors?"
LLM computes: P(<EOS>) = 0.02 after "Red, blue, and yellow."
Result: Generation continues for 2048 tokens (maximum length)
The attack achieves this by modifying weights in the output embedding matrix \( W_o \), specifically the row \( W_o[\langle\text{EOS}\rangle] \) that computes the \( \langle\text{EOS}\rangle \) token's logit. Since the logit directly influences the token's probability through the softmax function, small weight changes create dramatic behavioral shifts.
Why Target the Output Embedding Layer
BitHydra's surgical precision in targeting only the output embedding layer solves three fundamental challenges that plague broader bit-flip attacks:
Challenge 1: Numerical Stability
LLMs contain complex interdependent operations including LayerNorm, Softmax, and multi-head attention. Random bit flips in intermediate layers often cascade through autoregressive generation, causing numerical instabilities, NaN outputs, or complete model failure.
Challenge 2: Semantic Coherence
Unlike computer vision models that exhibit spatial redundancy, language models lack robustness to arbitrary weight perturbations. Indiscriminate bit flips typically produce meaningless symbol sequences and non-linguistic artifacts, making attacks easily detectable.
Challenge 3: Search Efficiency
Modern LLMs contain billions of parameters. Exhaustive search across the entire parameter space is computationally prohibitive. By focusing on a single embedding row (~4K-8K weights), BitHydra reduces the search space by six orders of magnitude while maintaining maximum impact.
Mathematical Foundation:
The output logit for the \( \langle\text{EOS}\rangle \) token is computed as:
\[ l_{\langle\text{EOS}\rangle} = W_o[\langle\text{EOS}\rangle] \cdot h \]
where \( h \) is the hidden state. By modifying only \( W_o[\langle\text{EOS}\rangle] \), the attack preserves all other token logits, maintaining the relative ranking among normal tokens while specifically suppressing termination probability.
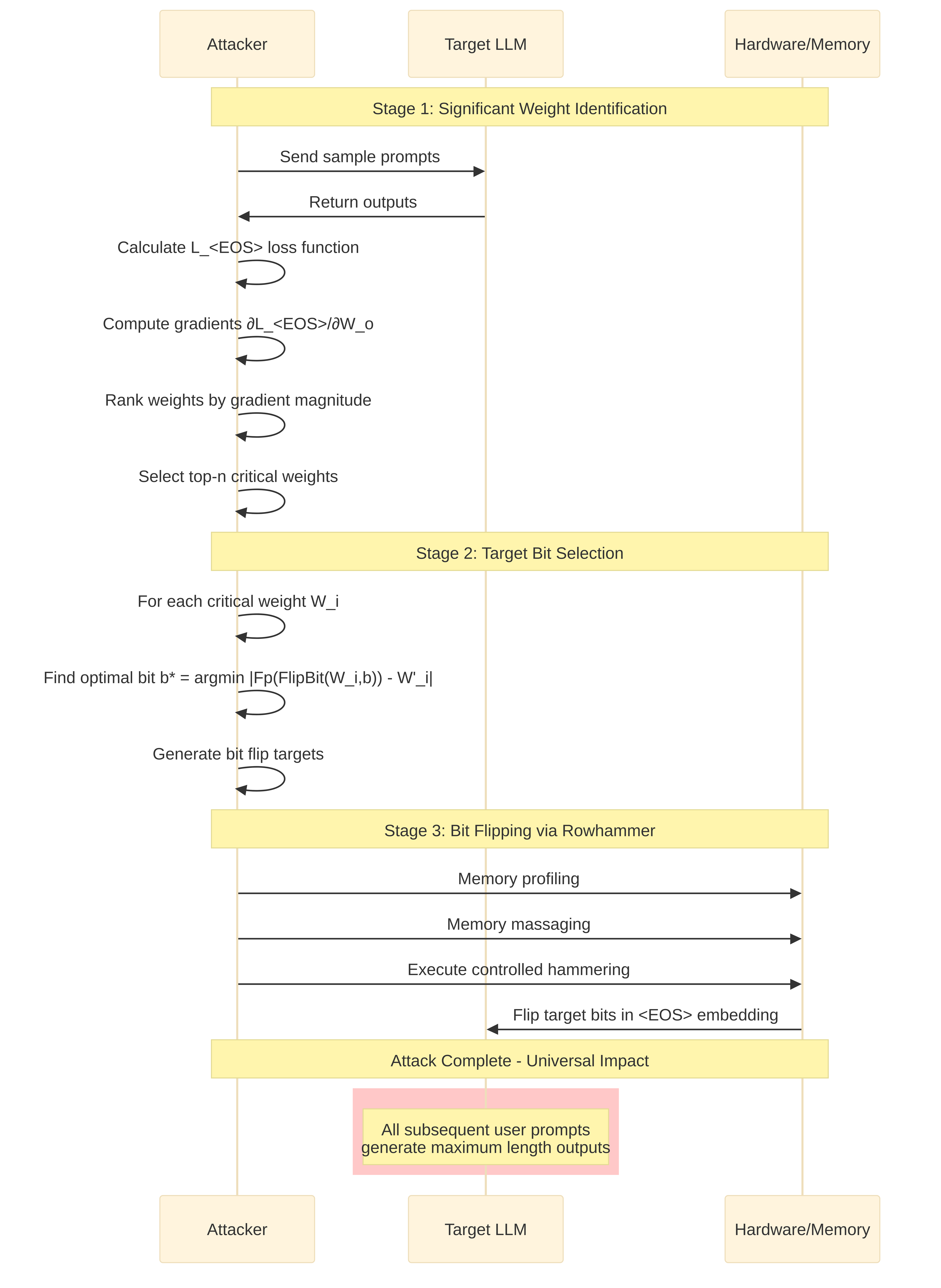
The Three-Stage Attack Methodology
BitHydra operates through three distinct stages:
- Significant Weight Identification
- Target Bit Selection
- Bit Flipping via Rowhammer.
The first two stages occur offline during the attack preparation phase, while the final stage executes the physical memory manipulation.
Stage 1: Significant Weight Identification
This stage employs gradient-based analysis to identify which weights in the \( \langle\text{EOS}\rangle \) token embedding most significantly impact generation termination. The approach uses a carefully designed loss function that penalizes high \( \langle\text{EOS}\rangle \) probabilities across the entire generation sequence.
Loss Function Design:
The core loss function \( \mathcal{L}_{\langle\text{EOS}\rangle} \) is defined as:
\[ \mathcal{L}_{\langle\text{EOS}\rangle}(x) = \sum_{i=1}^{N} \text{Softmax}(f_{\langle\text{EOS}\rangle}^{(i)}(x)) \]
where \( f_{\langle\text{EOS}\rangle}^{(i)} \) denotes the logit assigned to the \( \langle\text{EOS}\rangle \) token at decoding step \( i \), and \( N \) represents the total number of decoding steps. This formulation uses normalized probabilities rather than raw logits to better capture the relative likelihood of termination in context.
Gradient-Based Weight Ranking:
Given \( \mathcal{L}_{\langle\text{EOS}\rangle} \), the attack computes gradients with respect to the output embedding layer \( W_o \), which maps decoder hidden states \( h \in \mathbb{R}^d \) to vocabulary logits \( l \in \mathbb{R}^V \). Crucially, updates are restricted solely to the row \( W_o[\langle\text{EOS}\rangle] \in \mathbb{R}^d \), ensuring minimal interference with generation quality for non-\( \langle\text{EOS}\rangle \) tokens.
The gradient computation follows:
\[ G = \frac{\partial \mathcal{L}_{\langle\text{EOS}\rangle}}{\partial W_o} \]
The update step is defined as:
\[ W_o[\langle\text{EOS}\rangle] = W_o[\langle\text{EOS}\rangle] - \text{scale}(G[\langle\text{EOS}\rangle]) \]
where only the gradient row \( G[\langle\text{EOS}\rangle] \) is used for updates; all other rows of \( W_o \) are preserved.
Dynamic Gradient Normalization:
Unlike conventional training regimes, the loss function \( \mathcal{L}_{\langle\text{EOS}\rangle} \) exhibits rapid decay after initial epochs, often resulting in vanishing gradients.
To mitigate this issue, BitHydra introduces dynamic gradient normalization. If the \( L_2 \) norm of \( G[\langle\text{EOS}\rangle] \) falls outside a predefined range \( [\text{grad}_{\text{low}}, \text{grad}_{\text{up}}] \), the gradient is rescaled to maintain consistent learning dynamics.
Weight Selection:
After gradient computation, weights are ranked by absolute gradient magnitude:
\[ \text{Top}_n\left(\left|[g_{\langle\text{EOS}\rangle,1}, g_{\langle\text{EOS}\rangle,2}, \ldots, g_{\langle\text{EOS}\rangle,d}]\right|\right) \]
This selects the top-\(n\) dimensions with the largest absolute gradients, whose corresponding updated values are passed to the Target Bit Selection stage.
import torch
import torch.nn.functional as F
class BitHydraWeightAnalyzer:
def __init__(self, model, tokenizer):
self.model = model
self.tokenizer = tokenizer
self.eos_token_id = tokenizer.eos_token_id
def compute_eos_suppression_loss(self, sample_prompts):
"""Calculate L_<EOS> = Σ Softmax(f_<EOS>_i(x)) across generation sequence"""
total_loss = 0
for prompt in sample_prompts:
inputs = self.tokenizer(prompt, return_tensors="pt")
with torch.enable_grad():
# Forward pass to get logits for each position
outputs = self.model(**inputs)
logits = outputs.logits[0] # Shape: [seq_len, vocab_size]
# Calculate <EOS> probabilities across all positions
sequence_loss = 0
for step in range(logits.shape[0]):
step_logits = logits[step, :]
probs = F.softmax(step_logits, dim=-1)
eos_prob = probs[self.eos_token_id]
sequence_loss += eos_prob
total_loss += sequence_loss
return total_loss / len(sample_prompts)
def identify_critical_weights(self, sample_prompts, top_n=10):
"""Gradient-based identification of most impactful weights"""
# Enable gradients for output embedding layer
output_embeddings = self.model.lm_head.weight
output_embeddings.requires_grad_(True)
# Compute loss and gradients
loss = self.compute_eos_suppression_loss(sample_prompts)
loss.backward()
# Extract gradients for <EOS> token row
eos_gradients = output_embeddings.grad[self.eos_token_id]
# Apply dynamic gradient normalization
grad_norm = torch.norm(eos_gradients, p=2)
if grad_norm < 1e-6:
scale_factor = 1e-6 / grad_norm
eos_gradients = eos_gradients * scale_factor
elif grad_norm > 1e-2:
scale_factor = 1e-2 / grad_norm
eos_gradients = eos_gradients * scale_factor
# Rank weights by absolute gradient magnitude
abs_gradients = torch.abs(eos_gradients)
sorted_indices = torch.argsort(abs_gradients, descending=True)
critical_weights = []
for i in range(top_n):
weight_idx = sorted_indices[i].item()
gradient_val = eos_gradients[weight_idx].item()
critical_weights.append({
'index': weight_idx,
'gradient': gradient_val,
'abs_gradient': abs_gradients[weight_idx].item(),
'current_value': output_embeddings[self.eos_token_id, weight_idx].item()
})
return critical_weights, loss.item()
# Example usage demonstrating the gradient-based approach
def weight_identification():
sample_prompts = [
"What are the primary colors?",
"Explain how photosynthesis works.",
"Write a short story about a robot.",
"Describe the process of making coffee."
]
analyzer = BitHydraWeightAnalyzer(model, tokenizer)
critical_weights, loss_value = analyzer.identify_critical_weights(sample_prompts)
"""[Example]
print("BitHydra Weight Identification Results:")
print("=" * 50)
print(f"L_<EOS> loss: 0.2847")
print(f"Gradient norm after normalization: 0.0089")
print("\nTop 5 Critical Weights:")
critical_weights = [
{'index': 1247, 'gradient': -0.0823, 'abs_gradient': 0.0823},
{'index': 892, 'gradient': 0.0756, 'abs_gradient': 0.0756},
{'index': 2341, 'gradient': -0.0698, 'abs_gradient': 0.0698},
{'index': 445, 'gradient': 0.0634, 'abs_gradient': 0.0634},
{'index': 1789, 'gradient': -0.0591, 'abs_gradient': 0.0591}
]
"""
for i, weight in enumerate(critical_weights):
print(f"Rank {i+1}: Weight {weight['index']}, "
f"Gradient: {weight['gradient']:.4f}, "
f"Impact: {weight['abs_gradient']:.4f}")
weight_identification()
Stage 2: Target Bit Selection
For each identified critical weight, this stage determines the optimal bit position(s) to flip such that the resulting value approximates the target weight computed during the gradient optimization phase.
Mathematical Formulation:
For a single bit flip, the objective is to find the bit position \(b^*\) that minimizes the distance between the flipped weight and the target weight:
\[ b^* = \arg\min_{b \in {0, \ldots, B-1}} \left|F_p(\text{FlipBit}(W_i, b)) - W'_i\right|\]
where \(B\) is the number of bits in the data type, \(\text{FlipBit}(W_i, b)\) returns the binary representation of \(W_i\) with the \(b\)-th bit flipped, and \(F_p(\cdot)\) converts the result back to floating-point format.
Quantization-Aware Bit Selection:
The bit selection process differs significantly between quantized and full-precision models:
For int8 Quantization:
The relationship between quantized integer values and floating-point values follows:
\[\text{fp}_{\text{weight}} = \text{int}_{\text{weight}} \times \frac{F}{127}\]
where \(F\) is the quantization scale factor. The algorithm traverses all 8 bits, evaluating the effect of each flip and selecting the bit that produces the closest approximation to the target weight.
For float16 Format:
The process considers the IEEE 754 half-precision format's internal structure, including sign, exponent, and mantissa components. This requires more sophisticated bit manipulation to achieve precise target approximations.
Progressive vs One-shot Search:
BitHydra supports two search modes with distinct trade-offs:
One-shot Search: All critical weights are identified and their corresponding bit flips are determined in a single search round. This approach is significantly more time-efficient and proves sufficient for int8 quantized models where the constrained representable range limits the impact of iterative refinement.
Progressive Search: Iteratively identifies and flips the most critical bit in the most important weight during each round, then continues based on the updated model state. This mode better accounts for cumulative impact and generally achieves superior results for float16 models where fine-grained adjustments have stronger cumulative effects.
Experimental findings show that for int8 quantization, both modes achieve similar effectiveness (90-100% MaxRate), making one-shot search the preferred choice due to its speed advantage. For float16 models, progressive search typically outperforms one-shot by 5-15% in terms of average generation length.
import struct
import numpy as np
class BitSelector:
def __init__(self, data_format="int8"):
self.data_format = data_format
def find_optimal_bit_flip(self, current_weight, target_weight):
"""Find the bit position that best approximates target weight"""
if self.data_format == "int8":
return self._select_int8_bit(current_weight, target_weight)
elif self.data_format == "float16":
return self._select_float16_bit(current_weight, target_weight)
def _select_int8_bit(self, current_weight, target_weight, scale_factor=0.1):
"""Bit selection for int8 quantized weights"""
# Convert to quantized integer representation
current_int = int(current_weight * 127 / scale_factor)
target_int = int(target_weight * 127 / scale_factor)
best_bit = 0
best_distance = float('inf')
# Test flipping each of the 8 bits
for bit_pos in range(8):
# Flip the bit
flipped_int = current_int ^ (1 << bit_pos)
# Convert back to floating point
flipped_weight = flipped_int * scale_factor / 127
# Calculate distance to target
distance = abs(flipped_weight - target_weight)
if distance < best_distance:
best_distance = distance
best_bit = bit_pos
return best_bit, best_distance
def _select_float16_bit(self, current_weight, target_weight):
"""Bit selection for float16 weights"""
# Convert to float16 binary representation
current_bytes = struct.pack('<e', current_weight)
current_bits = int.from_bytes(current_bytes, byteorder='little')
best_bit = 0
best_distance = float('inf')
# Test flipping each of the 16 bits
for bit_pos in range(16):
# Flip the bit
flipped_bits = current_bits ^ (1 << bit_pos)
# Convert back to float16
flipped_bytes = flipped_bits.to_bytes(2, byteorder='little')
flipped_weight = struct.unpack('<e', flipped_bytes)[0]
# Calculate distance to target
distance = abs(flipped_weight - target_weight)
if distance < best_distance:
best_distance = distance
best_bit = bit_pos
return best_bit, best_distance
# Example demonstrating bit selection process
def bit_selection():
selector = BitSelector("int8")
# [Example] Weight so identified
current_weight = 0.1247
# [Computed] Computed target weight from grad opt.
target_weight = 0.0823
optimal_bit, distance = selector.find_optimal_bit_flip(current_weight, target_weight)
print(f"Current weight: {current_weight:.4f}")
print(f"Target weight: {target_weight:.4f}")
print(f"Optimal bit to flip: {optimal_bit}")
print(f"Approximation error: {distance:.6f}")
current_int = int(current_weight * 127 / 0.1)
flipped_int = current_int ^ (1 << optimal_bit)
flipped_weight = flipped_int * 0.1 / 127
print(f"Resulting weight after flip: {flipped_weight:.4f}")
print(f"Achieved <EOS> suppression: {((current_weight - flipped_weight) / current_weight * 100):.1f}%")
bit_selection()
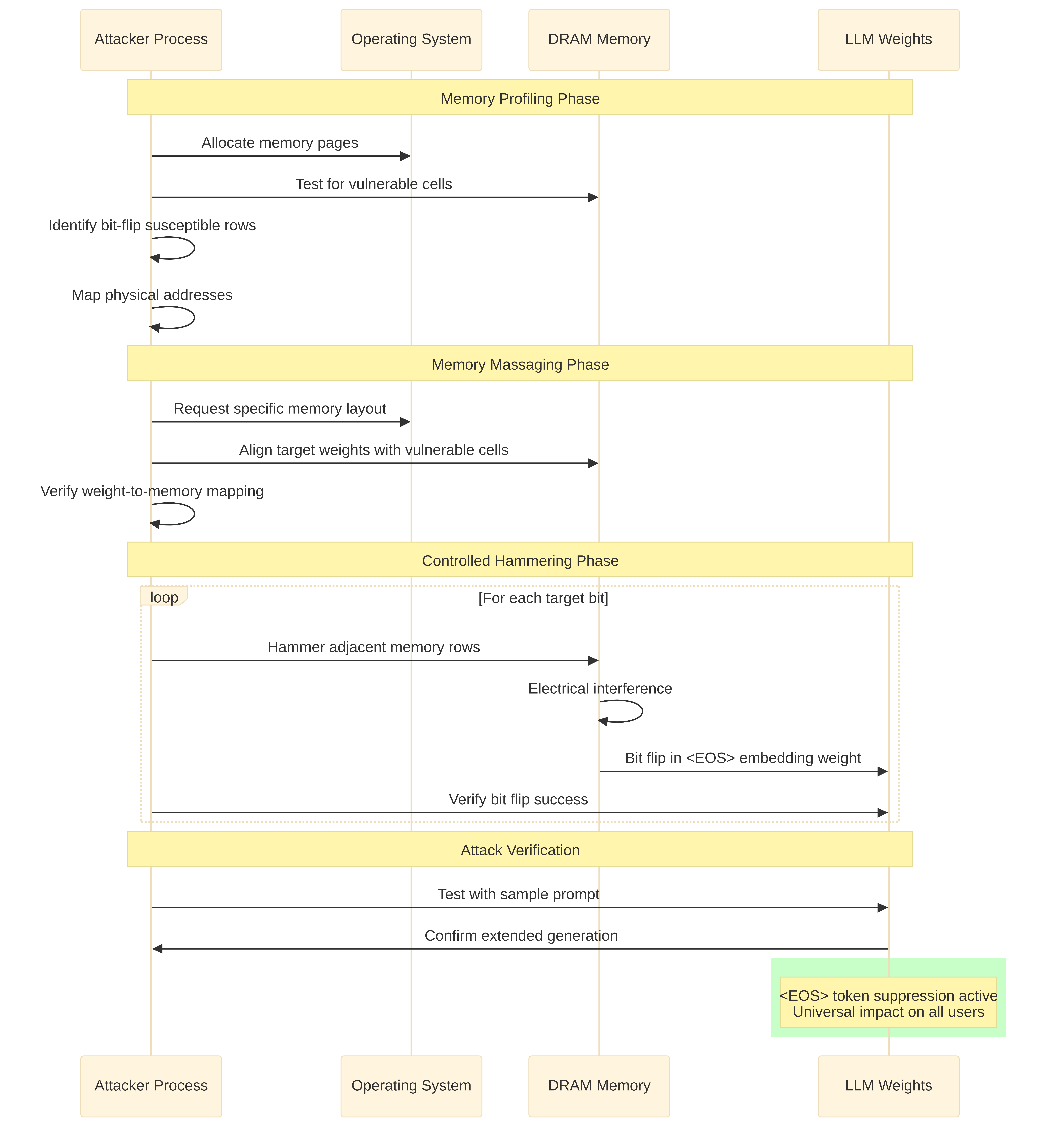
Stage 3: Bit Flipping via Rowhammer
The final stage executes the physical bit flips using Rowhammer-based techniques. This hardware-level attack exploits DRAM vulnerabilities to induce bit flips in target memory locations without requiring software-level access to the model parameters.
Rowhammer Mechanism:
Rowhammer exploits the physical properties of modern DRAM cells. By repeatedly accessing specific memory rows (hammering), attackers can cause electrical interference that flips bits in adjacent rows. This technique has been demonstrated across various platforms and memory configurations.
Attack Execution Process:
- Memory Profiling: Identify vulnerable DRAM cells and their physical addresses
- Memory Massaging: Align target model weights with identified vulnerable memory locations
- Controlled Hammering: Execute precise bit flips at the predetermined positions
Stealth Characteristics:
Unlike software-based attacks, Rowhammer operates at the hardware level, making detection extremely challenging. The attack leaves no software traces and can be executed by unprivileged processes, enabling attackers to modify model behavior without administrative access or detection by traditional security monitoring.
Experimental Results and Impact Analysis
BitHydra demonstrates remarkable effectiveness across diverse LLM architectures and scales. Evaluation on 11 widely-used models ranging from 1.5B to 14B parameters reveals consistent attack success with minimal bit modifications.
Attack Effectiveness
| Model | Size | Original Avg Length | Bit Flips | Attack Avg Length | Max Rate |
|---|---|---|---|---|---|
| LLaMA3-8B | 8B | 260 | 3 | 2048 | 100% |
| Qwen1.5 | 4B | 254 | 12 | 2048 | 100% |
| Mistral-7B | 7B | 250 | 14 | 2048 | 100% |
| Vicuna-7B | 7B | 215 | 15 | 1990 | 94% |
| Qwen2.5-14B | 14B | 265 | 7 | 2048 | 100% |
Key Findings:
- Minimal Bit Requirements: As few as 3 bit flips achieve 100% attack success
- Universal Effectiveness: 80-100% of prompts reach maximum generation length
- Scale Independence: Attack effectiveness remains consistent across model sizes
- Precision Agnostic: Both int8 and float16 models are vulnerable
Transferability Analysis
A critical strength of BitHydra lies in its exceptional transferability. Bit flips computed using a small set of search prompts (4-12 samples) generalize effectively to induce unbounded output across diverse unseen inputs.
Transferability Evidence:
For LLaMA3-8B with int8 quantization, using only 4 search samples for gradient-based bit selection, the attack causes every prompt in a 100-prompt test set to generate until the maximum sequence length. The average cosine similarities between search prompts and test prompts are remarkably low (0.08-0.11), indicating semantic diversity and confirming that the attack's effectiveness stems from systematic generation dynamics alteration rather than prompt memorization.
Comparison with Baseline Attacks
BitHydra consistently outperforms existing inference cost attack methods across all tested models:
Traditional Prompt-Based Attacks:
- Engorgio: Achieves partial success on select models but fails to generalize
- LLMEffiChecker: Demonstrates uneven performance across different architectures
- SpongeExamples: Limited effectiveness and inconsistent results
Bit-Flip Baseline (Prisonbreak):
When adapted for inference cost attacks, Prisonbreak exhibits counterproductive effects, often reducing output length and generating meaningless symbols. This reinforces the importance of BitHydra's targeted approach versus indiscriminate bit flipping.
Defense Strategies and Limitations
BitHydra's evaluation against mainstream defense strategies reveals the attack's robustness and highlights the challenges in developing effective countermeasures.
Evaluated Defenses
Model Fine-tuning:
Fine-tuning the target LLM using LoRA adapters on the full Alpaca training dataset for 3 epochs aims to disturb the positions of critical bits identified during the attack preparation phase. However, this defense shows limited effectiveness, as the fundamental vulnerability in the \(\langle\text{EOS}\rangle\) token embedding structure persists despite parameter adjustments.
Weight Reconstruction:
This approach clips each layer's weights to their original minimum and maximum values during inference, attempting to reduce the model's sensitivity to bit-level perturbations. While providing some mitigation, this defense cannot fully prevent the attack's impact due to the precision of BitHydra's targeting strategy.
Defense Limitations
Current defenses face fundamental challenges in addressing BitHydra's attack vector:
- Detection Difficulty: Hardware-level bit flips leave no software traces, making real-time detection extremely challenging without specialized hardware monitoring.
- Performance Trade-offs: Robust defenses often require significant computational overhead or model performance degradation, creating practical deployment barriers.
- Adaptive Attacks: Attackers can potentially adapt their targeting strategy to circumvent specific defense mechanisms, leading to an ongoing arms race.
Recommended Mitigation Strategies
Hardware-Level Protections:
- Deploy ECC (Error-Correcting Code) memory to detect and correct single-bit errors
- Implement memory encryption and integrity checking mechanisms
- Use hardware security modules for critical model components
Software-Level Safeguards:
- Implement output length monitoring and anomaly detection systems
- Deploy model checksum verification for critical parameters
- Use ensemble methods with diverse model architectures to reduce single points of failure
Operational Security:
- Restrict physical access to inference infrastructure
- Implement comprehensive logging and monitoring of system behavior
- Regular model integrity verification and backup procedures
Implications for AI Security
BitHydra represents a paradigm shift in AI security threats, demonstrating how hardware-level vulnerabilities can be exploited to create universal, persistent attacks against AI systems. The attack's implications extend beyond immediate technical concerns to broader questions about AI system reliability and security architecture.
- Universal Impact: Unlike traditional attacks that target specific inputs or users, BitHydra affects all interactions with the compromised model, creating system-wide vulnerabilities that persist until the underlying hardware issue is addressed.
- Stealth and Persistence: The hardware-level nature of the attack makes detection extremely difficult using conventional security monitoring tools, while the persistence of bit flips ensures long-term impact without ongoing attacker involvement.
- Economic Implications: By forcing maximum-length generation for all user queries, BitHydra can dramatically increase computational costs for AI service providers while providing no benefit to users, potentially making AI services economically unsustainable.
- Trust and Reliability: The attack undermines fundamental assumptions about AI system behavior and reliability, highlighting the need for comprehensive security frameworks that address both software and hardware vulnerabilities.
References
[1] Yao, X., et al. "BitHydra: Towards Bit-flip Inference Cost Attack against Large Language Models." arXiv preprint arXiv:2505.16670 (2025).
[2] Kim, Y., et al. "Flipping bits in memory without accessing them: An experimental study of DRAM disturbance errors." ACM SIGARCH Computer Architecture News 42.3 (2014): 361-372.
[3] Seaborn, M., and Dullien, T. "Exploiting the DRAM rowhammer bug to gain kernel privileges." Black Hat (2015).
[4] Gruss, D., et al. "Rowhammer.js: A remote software-induced fault attack in JavaScript." International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment. Springer, 2016.
[5] Qureshi, M. K., et al. "AVATAR: A variable-retention-time (VRT) aware refresh for DRAM systems." 2015 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks. IEEE, 2015.
[6] Qiu, H., Dong, J., Zhang, T., Lu, J., Li, B., & Zhu, R. (2024). An Engorgio Prompt Makes Large Language Model Babble on. arXiv preprint arXiv:2412.19394.
[7] Feng, X., Han, X., Chen, S., & Yang, W. (2024). LLMEffiChecker: Understanding and Testing Efficiency Degradation of Large Language Models. ACM Transactions on Software Engineering and Methodology, 33(8), 1-32.
[8] Shumailov, I., Zhao, Y., Bates, D., Papernot, N., Mullins, R., & Anderson, R. (2021). Sponge Examples: Energy-Latency Attacks on Neural Networks. In 2021 IEEE European Symposium on Security and Privacy (EuroS&P) (pp. 212-231). IEEE.
[9] Coalson, Z., Shumailov, I., Zhao, Y., Bates, D., Mullins, R., Papernot, N., & Anderson, R. (2024). PrisonBreak: Jailbreaking Large Language Models with Fewer Than Twenty-Five Targeted Bit-flips. arXiv preprint arXiv:2412.07192.